
You are tasked to analyse unknown malware samples detected by your SOC team.
One of the most useful techniques an analyst has at their disposal is hashing
SHA256 is not the only hashing algorithm you’re likely to come across as an analyst, though it is currently the most reliable in terms of balance of lack of collision and computational demand.
Because MD5 is known to be broken, it may be best to utilize a different algorithm.
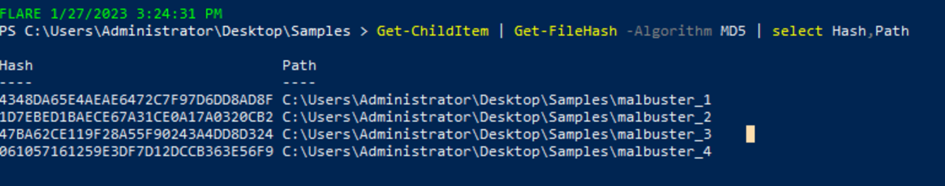
It should be apparent that utilizing our hashes first to search Virus Total may greatly assist in reducing triage time and confirm suspected attribution much more quickly than our own analysis may .
all answers up to question 6 are on Total Virus, if you don’t understand a question, take a breather and deepen your understanding of malware scanning.
Based on VirusTotal detection, what is the malware signature of malbuster_2 according to Avira?
The answer on virus total doesn’t fit the pattern on tryhackme , I recommend using https://metadefender.opswat.com/
Using the hash of malbuster_3, what is its malware signature based on abuse.ch?
Go on bazaar.abuse.ch in the browser part.
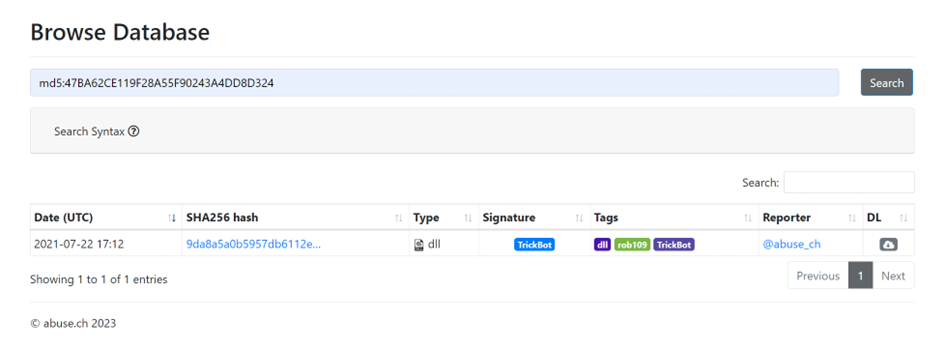
Using the hash of malbuster_4, what is its malware signature based on abuse.ch?
Same procedure.
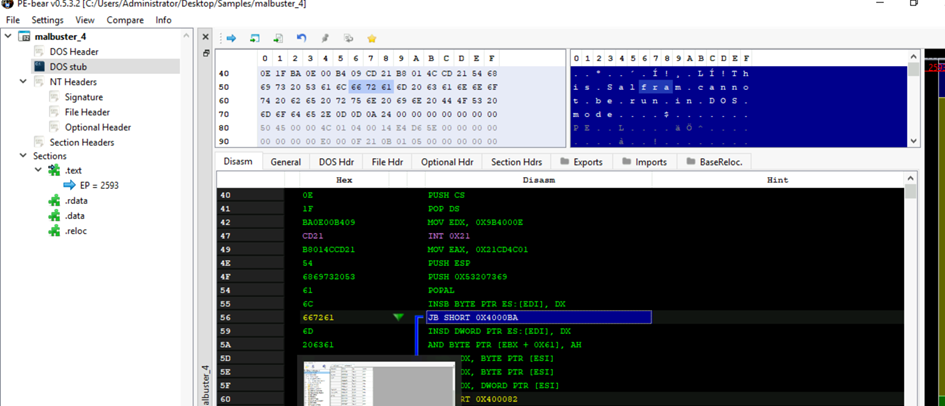
What is the message found in the DOS_STUB of malbuster_4?
Utilizing PEBear in our VM, we can examine the sections that are relevant to us within the DOS header.
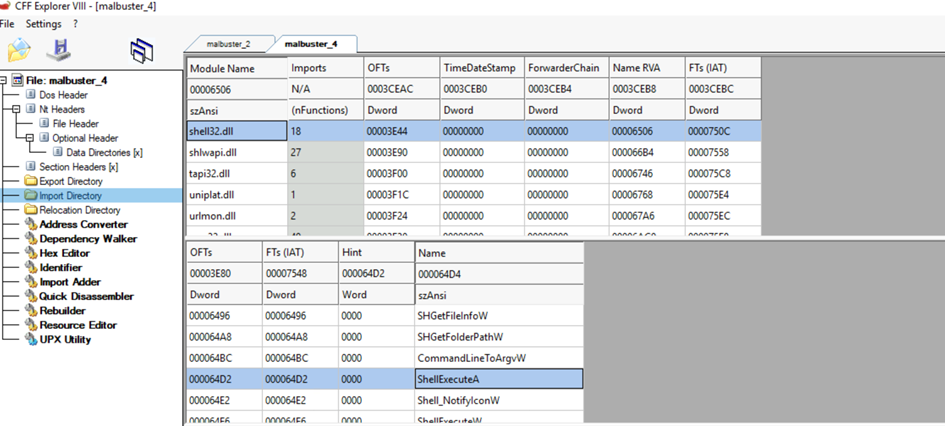
malbuster_4 imports the function ShellExecuteA. From which DLL file does it import this function?
Functions within DLLs allow both legitimate and malicious software authors to utilize pre-coded functions, which helps save time – as they do not have to code this functionality directly into their application and can utilize the built-in system functions from these DLLs. Selecting one of the imported link libraries will allow us to view the functions it imports from the libraries.
Virus total or cff explorer.
Using capa, how many anti-VM instructions were identified in malbuster_1?
“CAPA is a tool written by the FireEye/Mandiant FLARE team that can be used to quickly triage and assess capabilities of a malware sample.
CAPA provides a nice summary of the potential ATT&CK techniques the malware is using, along with its identified capabilities. This assessment can help in many malware analysis situations, but here the focus is on evasion techniques.”
Using capa, which binary can log keystrokes?
Use .\capa.exe. \Samples\malbuster_X on all the samples.
Which binary contains the string God Mode?
Get-ChildItem -Recurse | Select-String “GodMode” -List | Select Path
Which binary contains the string Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)?
Same procedure